Windows 8 includes a number of new and improved security features, here are some of them.
--------------------------------------------------------------------------
- Microsoft previewed a new touch-based security login at BUILD called picture password.
- Here's how it works: The user selects a picture, then makes three touch gestures on top of the image. The system remembers that sequence, and then the user repeats that sequence of gestures to login.
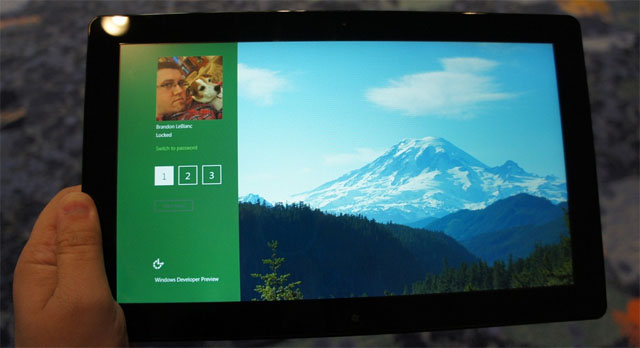
- For example, a user could have a picture of a pet as their startup screen, then use touch to draw a smile and touch both eyes of the dog.
- The gesture is tied to the image, and increases login security considerably. (Microsoft applied for a patent for the "sketch-based password authentication" technology behind picture password several years ago.)
- Microsoft explains that the system does not authenticate users based on an exact match of their drawing. “It authenticates based on the future similarity between an edge orientation pattern extracted from the sketch the user enters and an edge orientation pattern extract from the user’s pre-registered template sketch,” explains the patent filing.
- The feature, demonstrated below, is particularly useful for touch-based devices but also works well on a standard keyboard and mouse setup in Windows 8.
--------------------------------------------------------------------------
- Windows 8 supports the secure boot feature offered in the Unified Extensible Firmware Interface (UEFI), which should provide an additional layer of protection during the system startup process.
- Windows Secure Boot is a new feature that protects users against malware that affects the boot path. Common malware affecting boot path include boot loader viruses, boot sector viruses and rootkits that try to load as malware.
- Windows Secure Boot relies on allowing only signed and validated code to load during the boot process in order to the secure the boot path. If the code is unsigned, then the Windows Recovery Environment will be started which will try to fix the problem.
- This service will require UEFI based Secure Boot feature to function. A point to note is that, even though the code is validated during the boot process, Microsoft has managed to reduce the boot time in Windows 8 significantly.
-------------------------------------------------------------------------
- Social Engineering is one of the most dangerous weapons that the hackers have. Even the most tech savvy person can fall prey to these kinds of attacks if proper caution is not taken.
- IE9 already has a Smart Screen filter which will warn you when you try to visit a page with suspicious behaviour. With Windows 8, Microsoft is implementing this system wide. For this purpose, an application reputation database will be used.
- When you download a file, a reputation check is triggered and if the application that you downloaded is not rated, a message will be displayed warning the user.
- See the Actual Difference between what smart screen actually do in Windows 8 & what it means in Windows 7.
-------------------------------------------------------------------------
- OFFICIAL WINDOWS 8 READER
- One of the most noteworthy potential new features of Windows 8 from a security perspective could be the new Windows 8 integrated document reader, which will reportedly support PDF (and potentially more) file formats.
- PDF files and flash plug-ins have been notoriously porous from security point of view, and Modern Reader may signal a move by Microsoft to add yet even more default security to the Windows platform, a move that would echo recent statements about a move toward enhanced platform security made by other Microsoft executives.
An integrated Microsoft reader would undoubtedly be part of the unified Windows Update OS patching process, which removes the need for users (and admins) to worry about patching products from another vendor using a separate (and non-synchronized) update process, as is the case with Adobe's stand-alone product patching system.
That move does fit with Microsoft's recent move to a more aggressive security posture when it comes to making Windows (and other core Microsoft applications) as secure as possible, possibly at the cost of angering Microsoft partners like Adobe.
--------------------------------------------------------------------------
- EXPLOIT MITIGATION ENHANCEMENTS
- A number of improvements at the code level that give Windows 8 enhanced protection against software exploits, including improved Address Space Layout Randomization (ASLR), which works by "randomly shuffling the location of most code and data in memory to block assumptions that the code and data are at same address on all PCs."
- Windows kernel and Windows heap have been revamped with code improvements and integrity checks, respectively, that should harden Windows 8 and make it even more difficult for software exploits to work properly.
--------------------------------------------------------------------------










